Press reports today say Dr. Lisa Porter (Deputy Under Secretary of Defense for Research and Engineering) has been pitching an open source radio access network plan to major US networking companies. As we’ve explained, we need something like this to resolve the Huawei issue that’s holding up 5G rollouts by small networks.
While 5G’s greatest vulnerability is the massive software needed to stand up the network, software is also its greatest strength. To understand this apparent paradox, we need to back track a little.
The Internet is inherently insecure because its security model is based on the idea of a trusted community. In the beginning, nobody got access to the Internet but selected people, and all resources were available to all users. This was supplemented by a simple, one-time login at the periphery of each connected computer.
Trust in an Untrusted Community
That was a fine policy for a research network where everything was permitted except commercial activity – the original terms of use – but it doesn’t work today. The Internet is heavily intertwined with commerce and every criminal enterprise on the planet has a unit dedicated to exploiting it.
The original design trusted everyone: every machine was free to send information packets to every other machine anytime it wanted. This is embodied in the “connectionless” design of Internet Protocol. We’re moving to a state of affairs in which access to network resources must be barred by default until authorization is proved.
The new model is called “zero trust architecture” and the old model is called “perimeter defense.” Perimeter defense simply establishes that a user is known to be one of the good guys with access to essentially everything in a local network. Perimeter defense isn’t so hot when logins are compromised.
As the Name Implies, Zero Trust is Skeptical
Perimeter defense makes authentication, authorization, and accounting (AAA) a network function done by a firewall or the equivalent. Most big corporate networks used this model by default until relatively recently, and most of the small one still do.
One of the reasons that perimeter defense doesn’t work is that network administrators now login from everywhere so there’s really not a perimeter to defend. Another is that network resources writ large (including applications and databases) don’t legitimately need to be accessible to every employee.
Zero trust sees every resource as independent of all the others. It sets out to protect each and every resource from access by people with no legitimate need to do particular things to it. It may be fine for everyone to read a file, but not to modify, create, or delete it. And you better be who you say you are or you’re out of luck.
Zero Trust is Essential
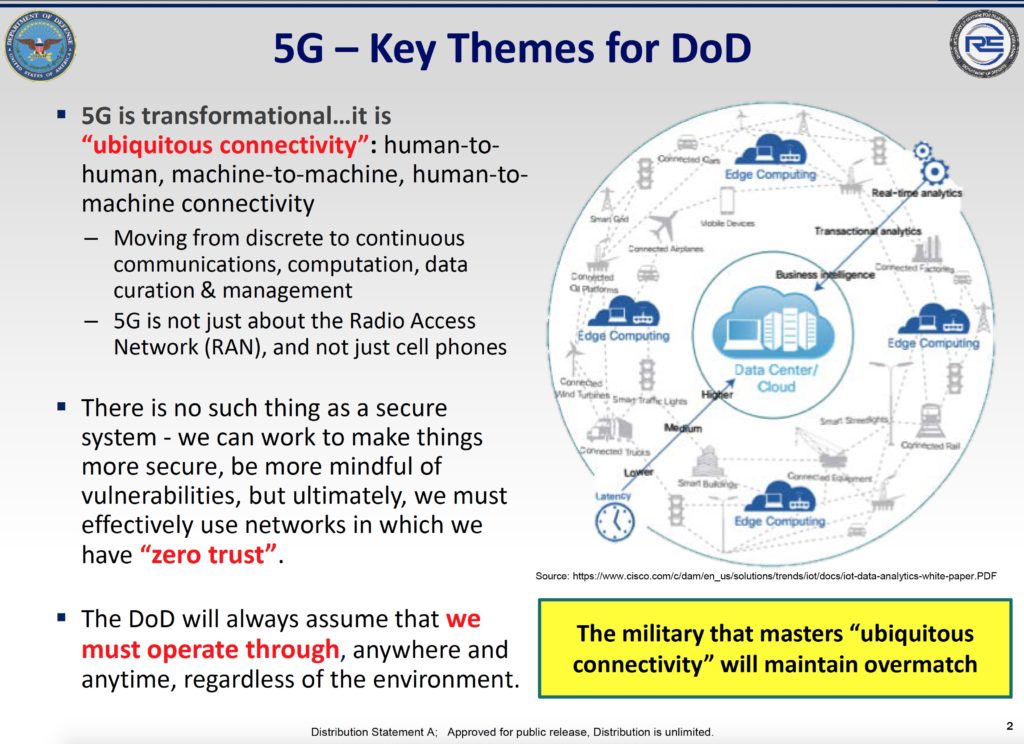
Porter gave a presentation on DoD’s approach to 5G at the Silicon Flatirons conference “Saving Our Spectrum: Handling Radio Layer Vulnerabilities in Wireless Systems” in October that I had the pleasure of attending. You can see the video here, but let’s focus on a few slides. Check the second bullet.
Because there is no such thing as a secure system, freeing the supply chain of untrusted actors such as Huawei doesn’t get us very far. In fact, the emphasis on particular suppliers can be a distraction that gives us a false sense of security just because one vulnerability is eliminated.
Just because a network is free of Huawei gear doesn’t mean it’s safe and secure. If we believe China is using Huawei as a Trojan horse to invade Western networks for the purpose of spying and disruption, don’t we have to entertain the notion that the country is also pursuing additional strategies toward the same goal, such as infiltrating the engineering teams at Ericsson and Nokia?
Scope of the Zero Trust Solution
The zero trust model addresses all threats, not just the ones that are easy to articulate. This is important because there are so many ways to compromise a network of computers housing valuable data that’s constantly updated – every business network in the world.
One of the requirements of zero trust is diversity of supply. On this front, the Huawei critics have a point. If every piece of equipment in a network comes from the same supplier – whoever it is – the network is vulnerable to bugs that happen to escape the supplier’s testing and certification procedures.
This is the case even if the supplier is a good guy, because most exploits are enabled by perfectly innocent bugs. Secure networks rely on diversity of supply and internal checking of data flows while the network is running. Lisa Porter gets this.
White Box Systems are More Secure than Single Vendor Solutions
White box network elements use open source software on commodity off-the-shelf (COTS) hardware. This approach goes a long way toward making networks more safe ands secure than they would be if built out of single vendor solutions.
Open source software is examined by dozens or hundreds of people at all stages of development, testing, and distribution. When one person finds and fixes a bug, all the users of that update potentially benefit. Open source is also visible to bad actors, but in most cases we can expect they’ll be outnumbered by good guys. And this is how it wins.
Reporters say big networking companies such as Oracle and Cisco are skeptical of open source radio access networks (RAN), but this is a bit misleading. Oracle certainly has a big stake in open source through its Java product and Cisco doesn’t even offer RANs.
5G Networks Interconnect with the Internet
5G networks aren’t islands, they’re parts of the global Internet that interconnect with the big switches made by Cisco, Juniper, Huawei, Ericsson, et al. These networks connect applications on end user systems with servers in the cloud.
Each network is a vantage point for observing the behavior of all the other systems, but each vantage point is limited. Hence, we can achieve security in Internet systems by aggregating information about data flows and constantly looking for anomalies. Security is a machine learning problem.
More than anything, we need network components that are inexpensive and capable of taking part in a comprehensive system of self-checking. We’re more likely to get such a system by building it collaboratively.
This is why open source, white box systems are more secure over the long that single vendor solutions. Computer people know this for the most part, but I’m not so sure about the self-styled experts whose analysis hasn’t got past the nameplate.
It’s good that DoD is on the right side of this debate, and it would be even better if Silicon Valley joined the party.
The post 5G and the Zero Trust Security Model appeared first on High Tech Forum.